P-Cert® - Professional certificate management
"Progress and Innovation Redefined: The next generation of security with Crypto Agility".
„
"Progress and Innovation Redefined: The next generation of security with Crypto Agility".
„

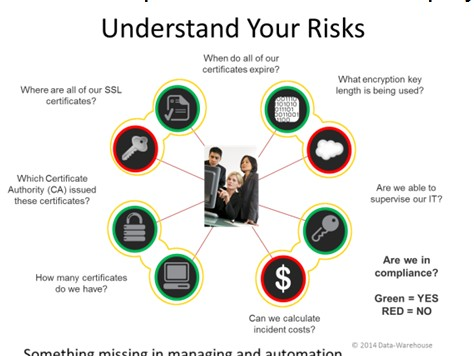
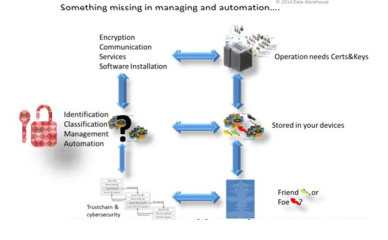
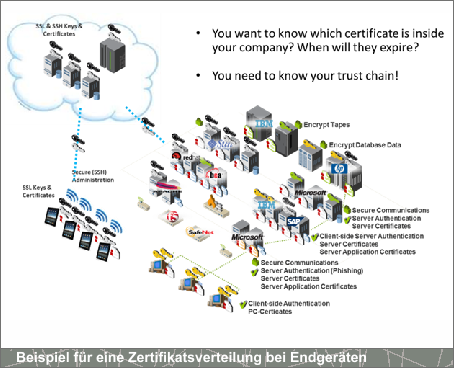
and complete overview of the internal IT trust and security base, such as X.509 certificate landscape, key handling and weakness identification
are solved early and preventively.
both medium-sized and large corporate networks
that are often stored or used undetected in your crypto landscape.
for verification, supplier auditing or preparation of a realignment of the PKI or crypto infrastructure.
A business incident caused by certificates in a company costs about $3-5 million in damages (source Ponemon & Gartner). A company typically experiences 3-5 incidents per year.
Imagine if you could prevent just one of them! Or even all of them?
Uncovering the unknown is the simple approach and business case of our PCert by Data-Warehouse product suite with more than 10 years of research and product experience in cryptographic processing. We help your company, vendors and customers build a comprehensive cryptographic inventory to reach the next level of security with a transparent and minimally invasive integration, enhancing your existing product and network structure with maximum automation and new features: preparing, migrating to the post-quantum era, reviewing and auditing your enterprise security processes, products and supply chains, ensuring product compliance and automating your administrative processes such as. such as certificate handling or information sharing within your operations and business continuity teams, and reducing the workload of your administrative teams through automation.
PCert® enables automatable, holistic investigation and management of the enterprise-wide internal X.509 certificate and risk landscape to prevent or resolve problems at an early stage. PCert® Security Suite supports organizations and enterprise networks and optionally provides knowledge- and service-based decision support.
The entire PKI process - from identification and evaluation to certificate deletion, replacement or acceptance - can be fully automated. Virtually all systems (including servers, devices and PCs running any operating system with JRE or Linux or Microsoft OS) can be included in these automated processes. You are able to enforce and automate your corporate policies in the X.509 world or migrate your current policies to the new world. PCert® addresses cybersecurity, business continuity and compliance simultaneously.
Your next level of cybersecurity: Eliminate cryptographic silos
The holistic approach of PCert® allows to investigate, discover, assess, automate and manage a very wide range of IT trust relationships, whether they are web services, products or devices. The PCert® approach is to identify every certificate, key (e.g., ssh, pgp), and keystore in every device to detect vulnerabilities, human or systemic errors, prevent infrastructure, program, and product problems, and prepare for or execute the transition to new technologies (post-quantum is already on the horizon). The benefits of PCert® are not only the full visibility of your technical environment and Public Key Infrastructure (PKI), but also the improvement of your cybersecurity, including your supply chain and the demonstration of compliance with various standards (SOX, ISO,...).
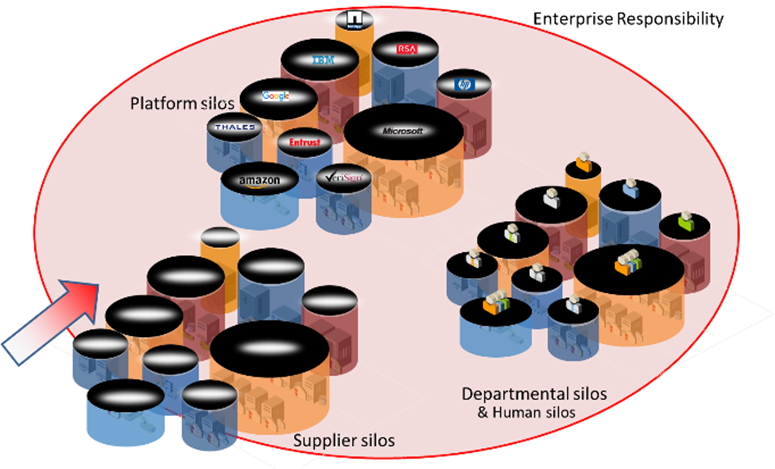
This also allows you to review chains of trust, supplier and vendor security, supply chains, and identify risks when using products in your infrastructure. Starting from sensors to complex products, whether state of the art or legacy, whether on premise or cloud or hybrid, whether your products, your infrastructure or your customer environments.
PCert recognizes your computer trust relationships (crypto assets such as X.509, SSH, PGP, Keystores) wherever and whatever they are and helps you manage them according to your corporate rules independent of individuals and silos and enhance your cybersecurity approach (SOC, CIT) with a new capability that extends your existing security products.
Your first step to knowledge begins with a PCert scan.
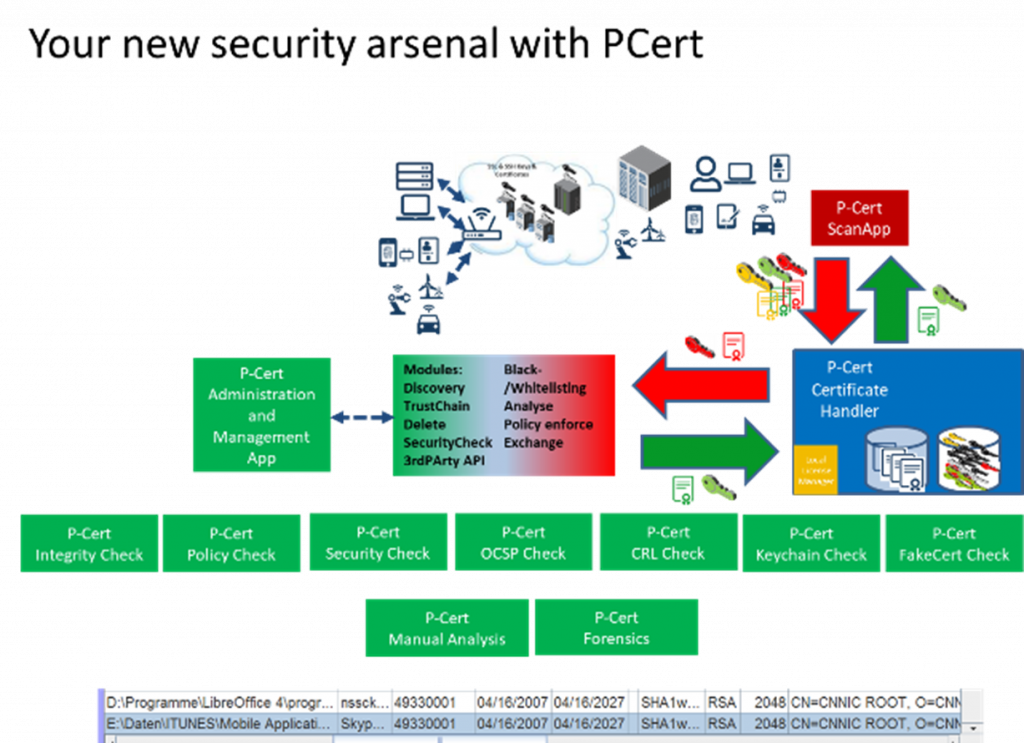
PCert scanner: your cryptographic inventory
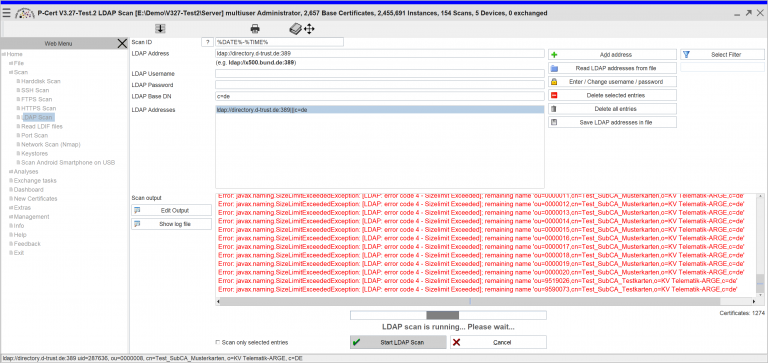
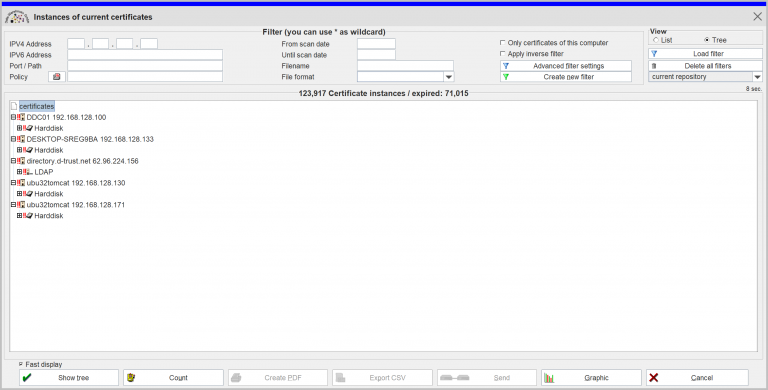
Enables your organization to collect and monitor all X.509 certificates, keystores (+ keys) residing on your computers (up to 400k each), servers (up to 200k each), or any other devices and create an enterprise-wide, holistic view and risk assessment for regulatory compliance (e.g. SOX, ISO 27.001) or preparing redesigns in trust landscapes. Since the products in your organization will constantly change, you always have an up-to-date status and can react immediately to changes. The scan engines update the database according to your individual requirements and the data is stored on-site (encrypted) and never leaves your boundaries. The flexibility and continuous improvement of the scan engines enables in-depth analysis of your IT's security and new insights to prevent incidents. This allows you to significantly reduce intrusion or vulnerability detection and management time.
This inventory is the most important step also for preparing migrations to future technologies.
Request a demo today or test it with a demo version. Just visit our website to do so. AWS/Azure in preparation
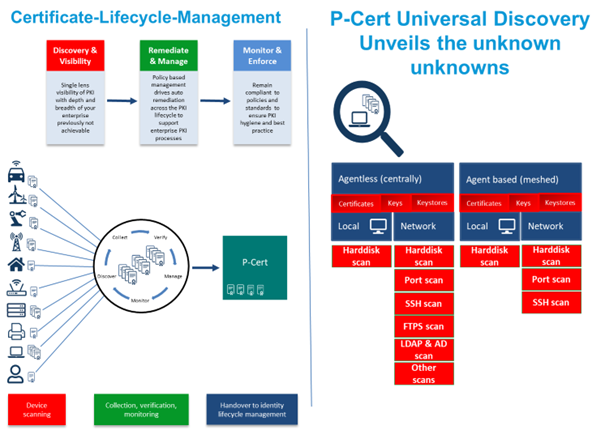
PCert Certificate Management Center
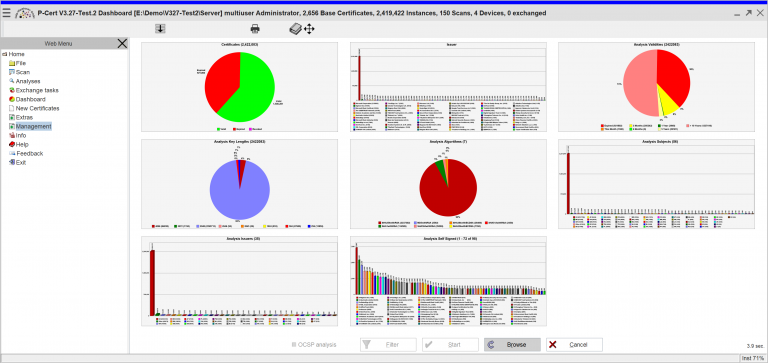
Collects all scanned results and creates an enterprise-wide risk map. You are able to enforce policies, share certificates and enroll them on devices. PCert enables you to manage and audit your IT trust landscape, helping you understand and identify even unknown cyber risks or vulnerabilities. Combined with audit gates and advanced filtering and reporting capabilities, you get your individual status in real-time and fact-based.
Proactive risk management process
PCert enables organizations to establish proactive certificate risk management processes to enhance the existing basic certificate management process with enhancements:
- Allow/Disallow Lists
- Delete/Disseminate
- Malware Testing/Supply Chain Vulnerabilities
- Online Monitoring with Analysis of Impact of
Status Changes
- Audit of Gateways and Forensic Analysis
- Identify Unwanted Trust Anchors
- Prepare and Execute a Vendor Exchange
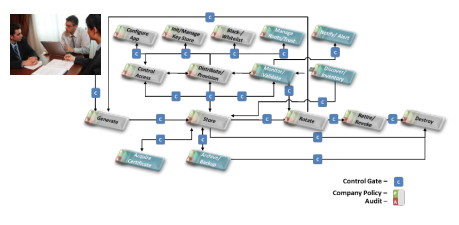
Some examples of our diverse technology capabilities for identifying and managing your IT trust dependencies:
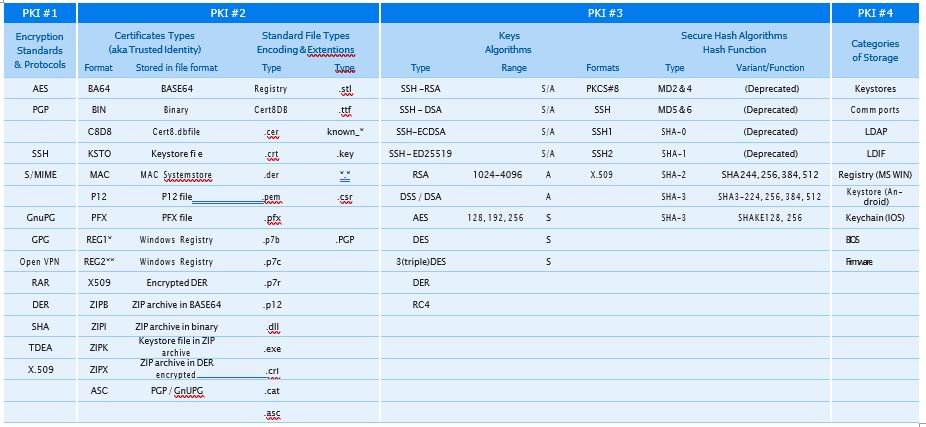
Rollout is as simple as you need it to be in your infrastructure, including options for meshing and autoupdating for all operating systems to minimize your administrative overhead and let you focus on your other tasks:
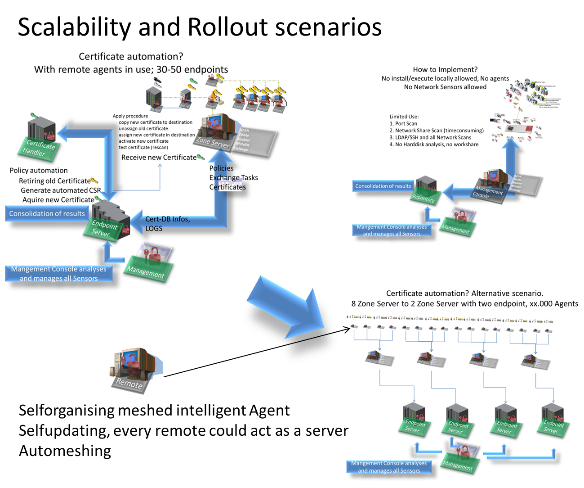
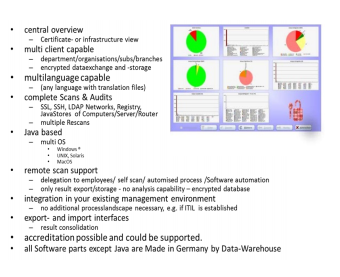
PCert provides an automatable, holistic overview of the enterprise-wide internal X.509 certificate and risk landscape to prevent or resolve problems at an early stage. PCert Security Suite supports both medium and large enterprise networks and optionally provides knowledge- and service-based decision support. The entire process from identification and assessment to certificate deletion, replacement or acceptance can be fully automated. Almost all systems (including servers, devices and PCs running any operating system with JRE or Linux or Microsoft OS) can be included in these automated processes. You are able to enforce and automate your corporate policies in the X.509 world.PCert addresses cybersecurity, business continuity and compliance issues.
Background:
Certificates are issued by many authorities. For a certificate to be considered valid, the issuing authority (CA) must be trusted. For this reason, many certificate authorities are trusted by default in web browsers. However, many of these companies and organizations are unknown to most users. De facto, the user must delegate trust to the software vendor or its supplier. A second problem is that it is even more difficult to make decisions about the certificate, such as how secure the procedures are that are used in its issuance and publication, and whether the certificate is even suitable or intended for which applications. The user should read the CA's Certificate Policy (CP) and Certification Practice Statement (CPS) for appropriate documentation, the contents of which are generally specified by RFC 3647. Qualified certificates can be used for high security requirements whose issuers are subject to legally mandated security standards and government oversight. However, government organizations may also request certificates from issuing authorities for their own purposes. This would authorize any surveillance software and allow clandestine installation by the country's national institutions (e.g., North Korea v. Sony®, China v. U.S. military aircraft industry).

This issue was highlighted, for example, by an incident in which VeriSign® issued certificates to people who falsely claimed to work for the Microsoft® company. For example, it would have been possible to sign program code so that it would be installed by Windows operating systems without warning on behalf of Microsoft®. Although these certificates were revoked immediately after the error became known, they still posed a security risk because the certificates contained no indication of where a possible revocation could be retrieved.
The Foxconn® certificate was also stolen and was the basis for the successful Kaspersky® hack. This case is a sign that one cannot blindly rely on the trustworthiness of certificates and the maintenance of CAs by operating systems and other software. Furthermore, the above press releases prove that even leading software vendors and experts are not yet fully aware of the issue. Certificate revocation is only effective if up-to-date revocation information is available for verification. For this purpose, certificate revocation lists (CRL) and online checks (e.g. OCSP) can be retrieved. Each browser, operating system, and application uses a vendor-dependent system for these checks. Currently, a named method is provided.
This issue can no longer be solved manually. This is where PCert comes into play.
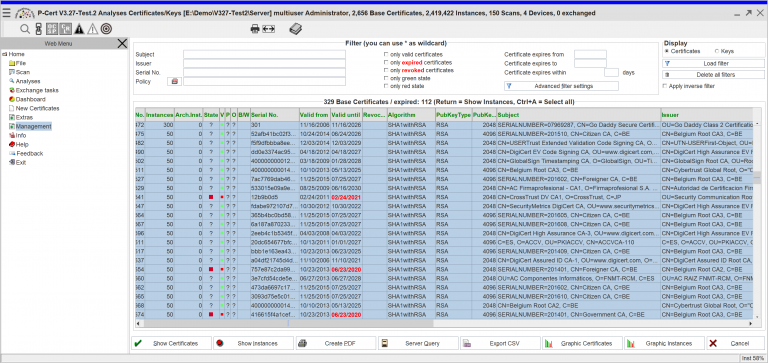
There are two approaches to obtaining an overview of the internal structure: The user only has trusted software installed and obtains an overview of the manufacturer's certificate. The user verifies the certificate landscape with an automated software solution and defines his trust landscape himself. Both approaches require knowledge of the complete trust landscape. This overview can be achieved with the PCert Scanner. This module allows you to examine the devices in your local network or remotely, manually or automated, serially or in parallel, and to manage them in a central repository (PCert Repository).
This on premise (cloud, hybrid) repository provides knowledge-based certificate assessment (manager) and trust chain verification (trust chain), removal of unwanted trust relationships (manual (delete) or service-based (CaaS)), risk identification (manual (analysis and security) or service-based), and corporate policy enforcement (policy) for automated certificate identification, handling, and distribution (remote). For automated management of complex networks, PCert ZoneServer supports the collection and automated distribution of policies and results to your endpoint (remote). Alternatively, the information can be collected on devices using automated software distribution processes. With encrypted local storage of results in the PCert Scan DB, any business process related to operations and software distribution can be supported.
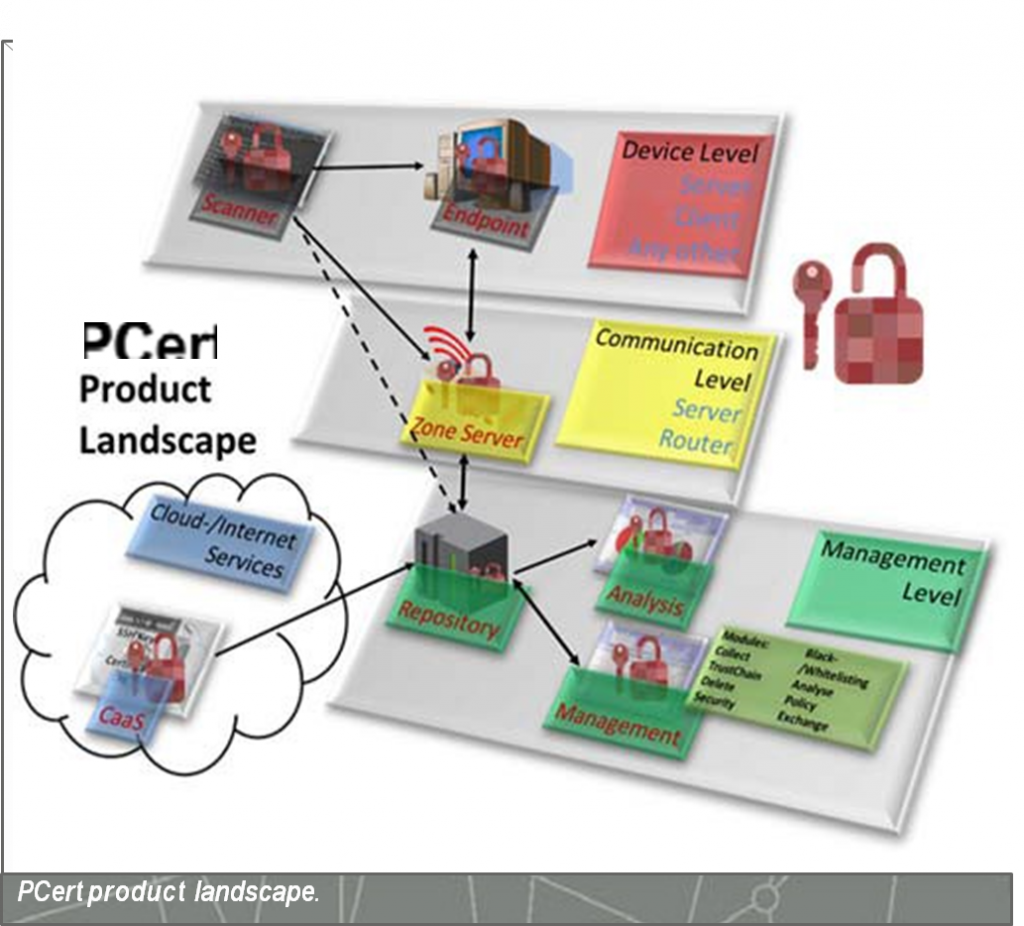
Our flexible API interfaces enable transparent and fast integration into your existing solution landscape. Should a company require a different process, appropriate adjustments are made within the PCert process engine (driven by EBUS-J) definitions so that it can be optimally integrated into the corporate process landscape. Our many years of experience in the creation of large, scalable, military and aeronautical software products are incorporated into the development of PCert and guarantee the highest software quality. In addition, Security by Design methodologies and regulatory requirements such as GDPR have been incorporated into our products from the outset, so that excellent state-level security can be achieved with minimal effort if required. No information is shared with third parties without explicit authorization.
Management suite with the following modules:
-> Collect (consolidation of scans)
-> TrustChain (chain of trust tests)
-> Delete (deletion and recovery)
-> Black-/ Whitelisting (allow / revoke)
-> Security (identification of risks)
-> Analysis (analysis and forensic functionality)
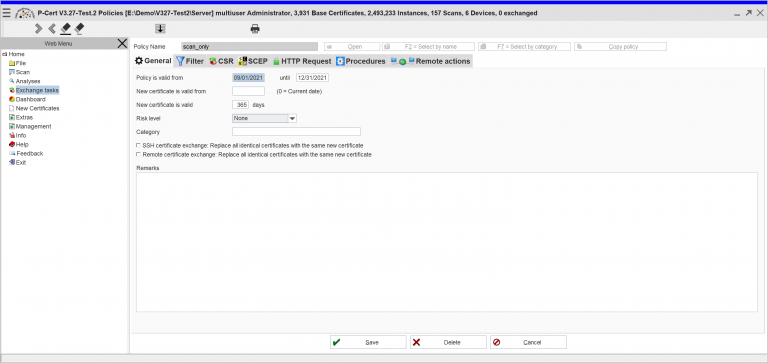
-> Policy (corporate guidelines (compliance))
-> Exchange (Automated Exchange)
Transmission of crypto asset information through network segments or creation of segments
Terminal management component with the following functions:
-> Identification (scanner)
-> Enforcement of policies incl. deletion
-> Enforcement of blacklisting/whitelisting
-> Constant monitoring of certificates by experts
-> Online database for suspicious certificates with
-> Update of the blacklisting DB
-> Extension of internal security assessments with online classification according to agreed security levels
Overview of:
GUI versions (for comfortable operation)
(single or groups of certifications)
Assignment of policies by